From losing a point or two on a school test to losing millions of dollars, we'll discuss how seemingly silly typos can have a huge impact on our lives. Sometimes unintentionally, but often times on purpose.
Misspelling a website
Or we may say it typosquatting. It's a deceptive practice where cybercriminals register misspelled versions of popular website domain names. This is an extremely common pattern. Typically similar domain registrations will spike when a product/service is on trend, or when a major event is ongoing or is upcoming.
At the time of writing, I've lost many examples of working URLs that lead to suspicious websites, without having the opportunity to take screenshots and analyze them. That's unfortunate. Some are no longer registered and some have been taken over by the organizations involved, for example, facebok[.]com—instead of facebook.com and offlice365[.]com—instead of office365.com. In the old days, when I tried to visit these sites after they were identified as suspicious, Chrome would fill our screen with a solid red, telling us that the page could not be loaded.
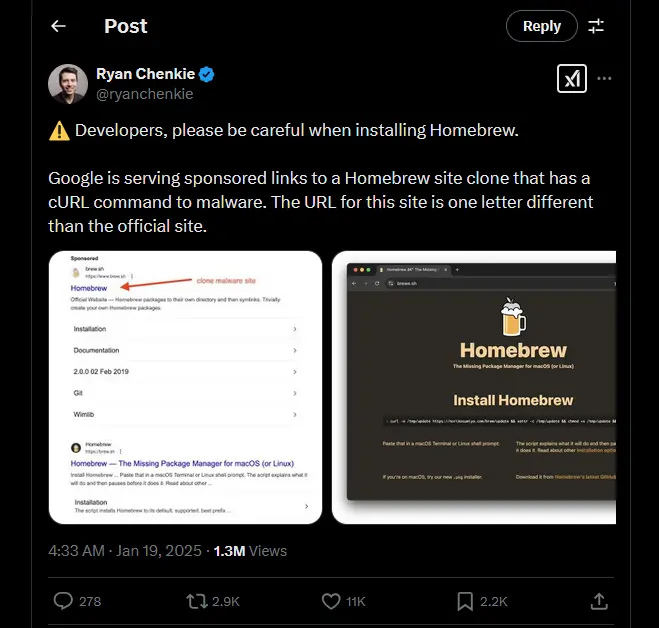
Don't lose hope yet, as there are still many cases even though not so popular. A month ago, Ryan Chenkie posted on X that he had discovered that Google was sponsoring a malicious Homebrew clone site at brewe[.]sh. The best, yet the scariest, part was that the site appeared as brew.sh in the search results.
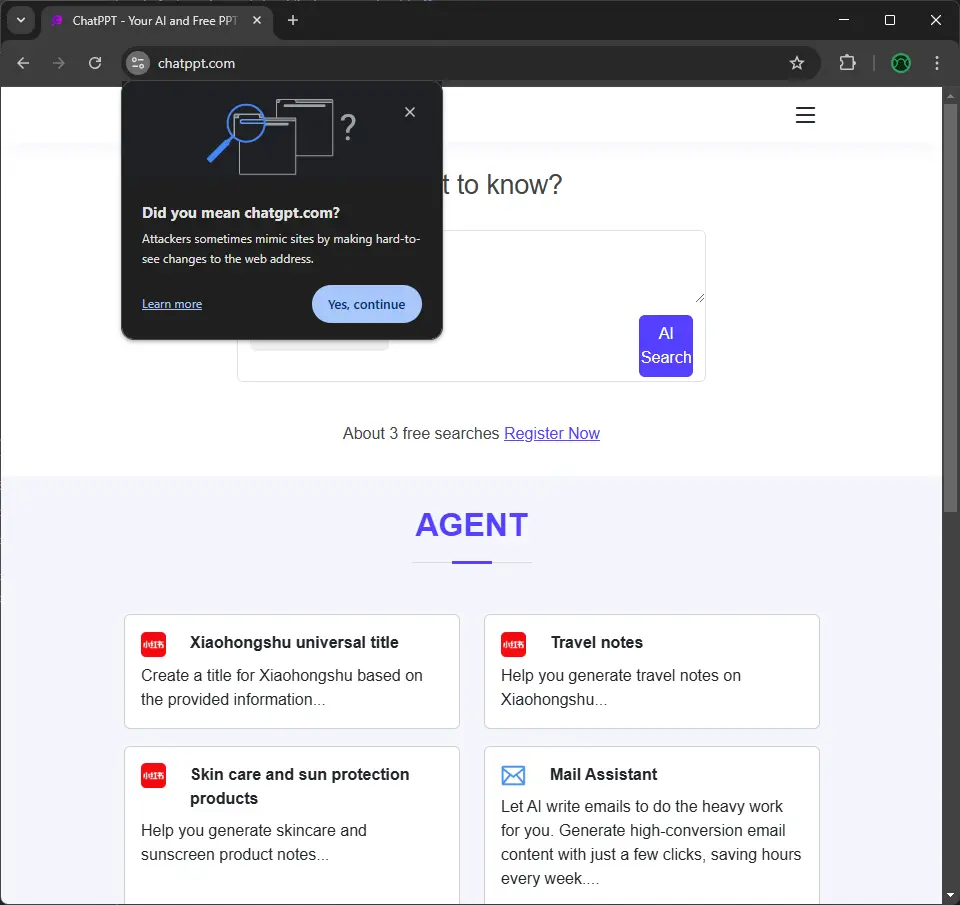
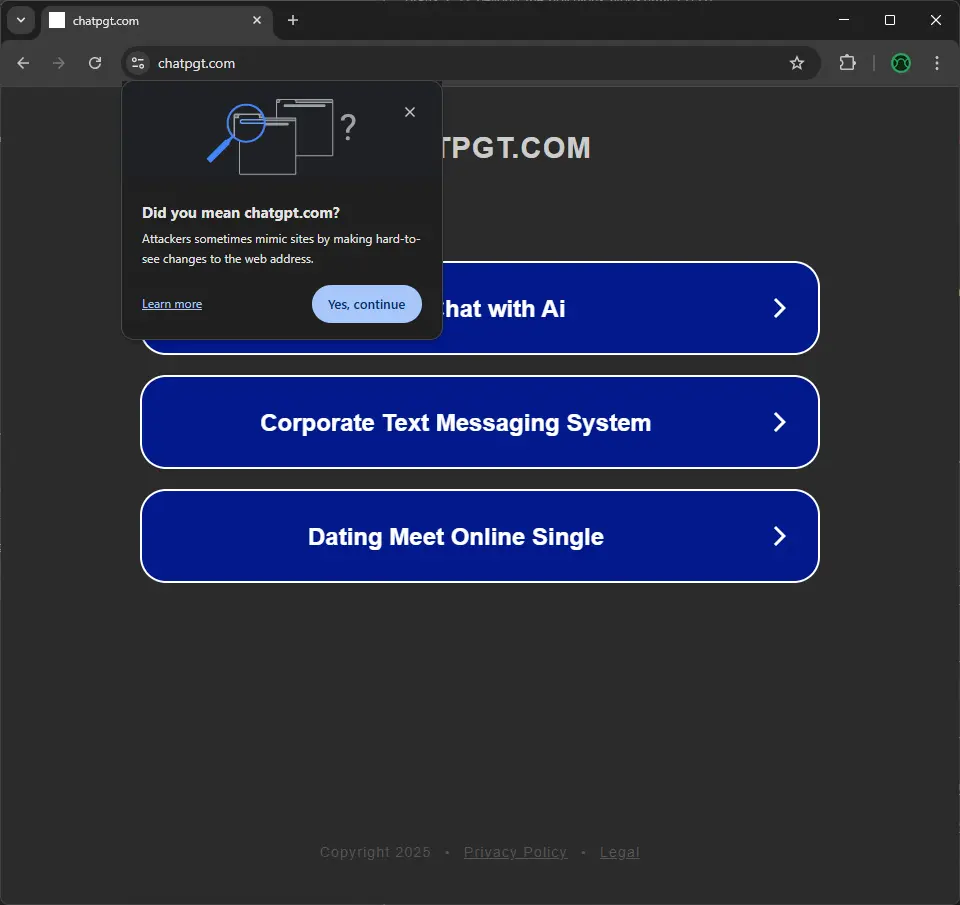
Nowadays, when we try to visit a website which likely contains typosquatting, we get a warning in the address bar. Look at these screenshots when we try to visit chatpgt[.]com and chatppt[.]com.
It doesn't have to be a single word difference, instead we can have a different root domain, chatgpt[.]org for example as an alternative for chatgpt.com.
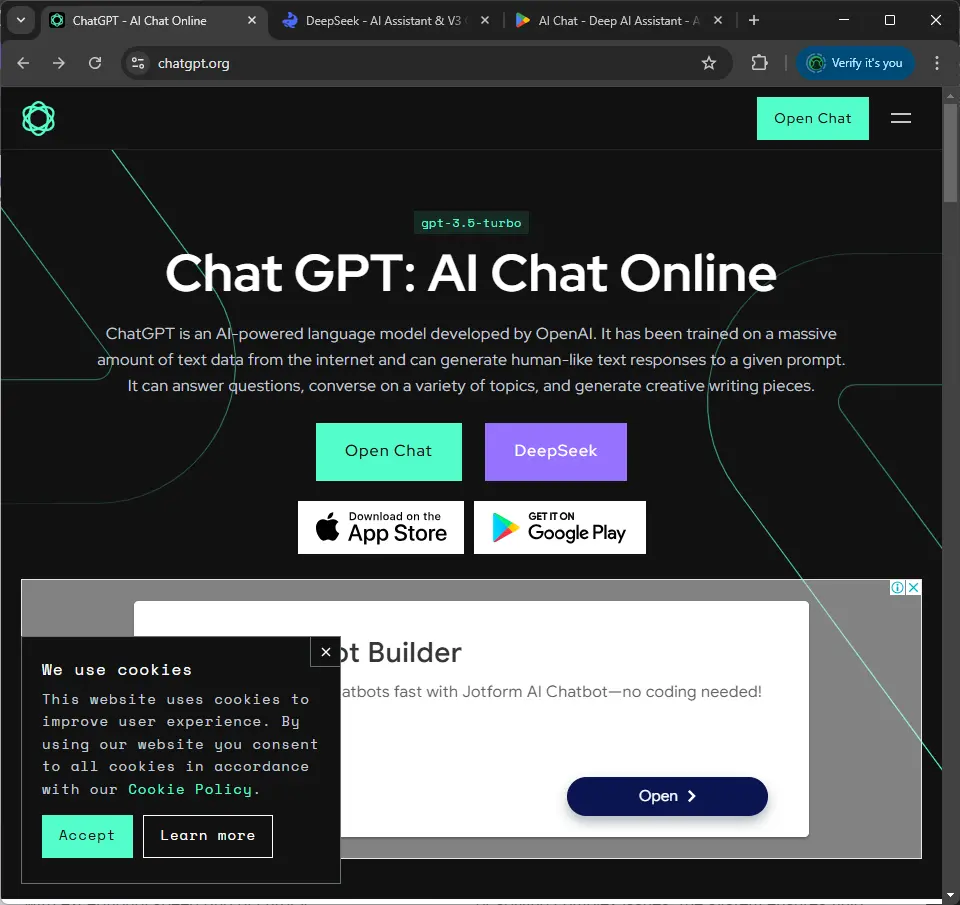
At the first glance, it doesn't look suspicious, right? We may know that it's not an official website, but some people deliberately look for alternatives so that they can use the service/product more freely, for example without being limited by the maximum number of prompts or anything that makes sense.
Clicking on the Get it on Google Play button, it'll direct us to the official Google Play page.

Again, it looks legit. One million downloads and 4.6 stars. What a great reputation! But not after we read some reviews. Not the ones with five stars of course. It may still contain bias such as hate speech. I'll let you judge for yourself.
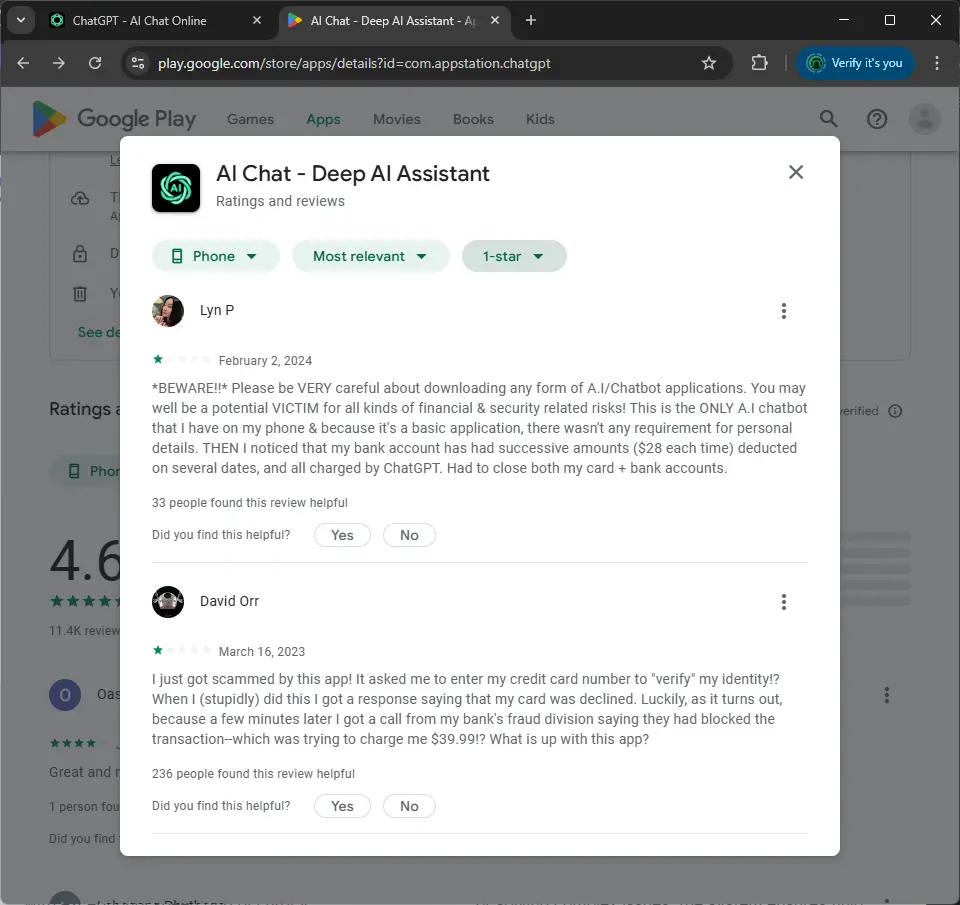
We're going to look at one more example. This time it involves DeepSeek. Way more different from deepseek.com which is written as deepseekchat[.]ai, but who cares? Not everybody knows which is the real one. I, myself, don't know either.
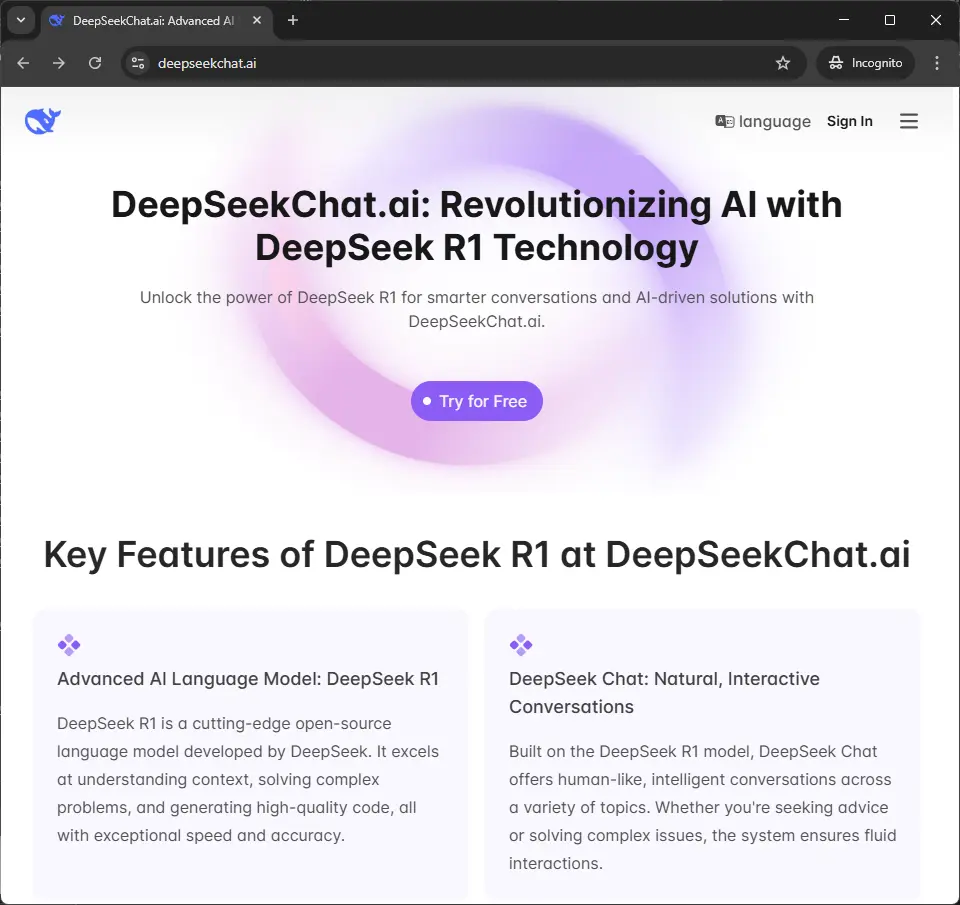
The landing page feels even friendlier than the official one. No Chinese characters, no benchmark tables, which are completely irrelevant to most people. Let's try to click on the Try for Free button.
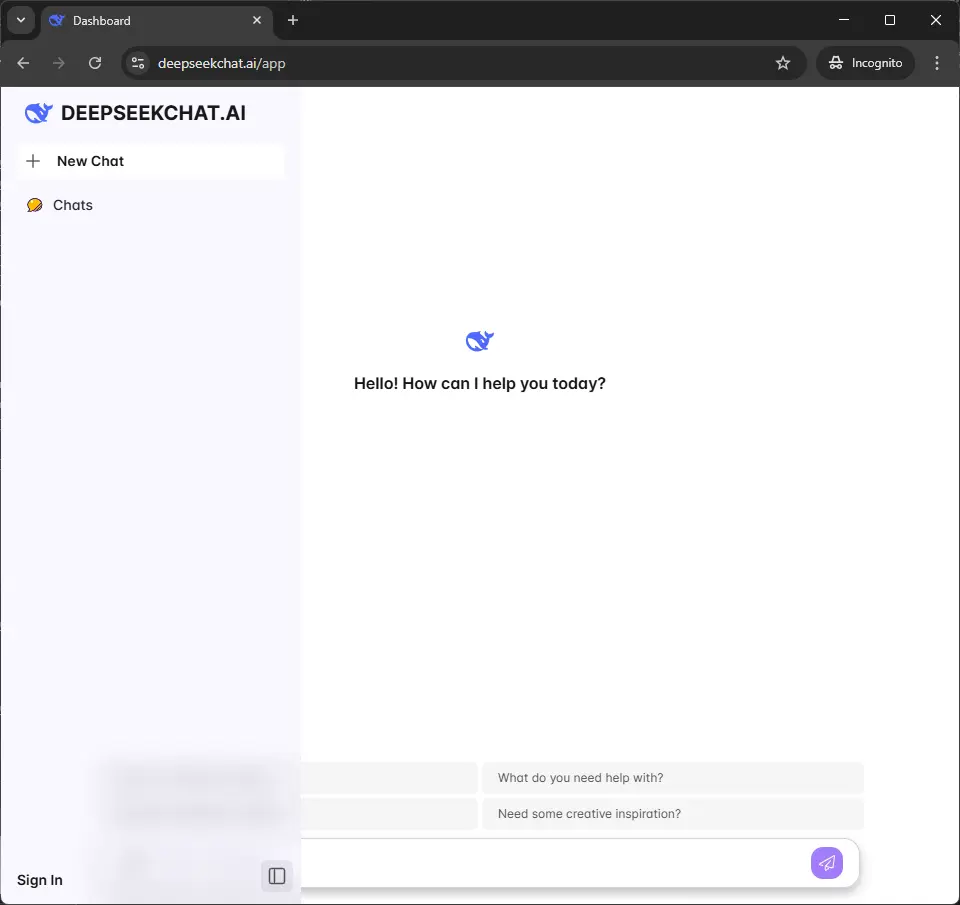
Okay, nice interface! Shall we log in?
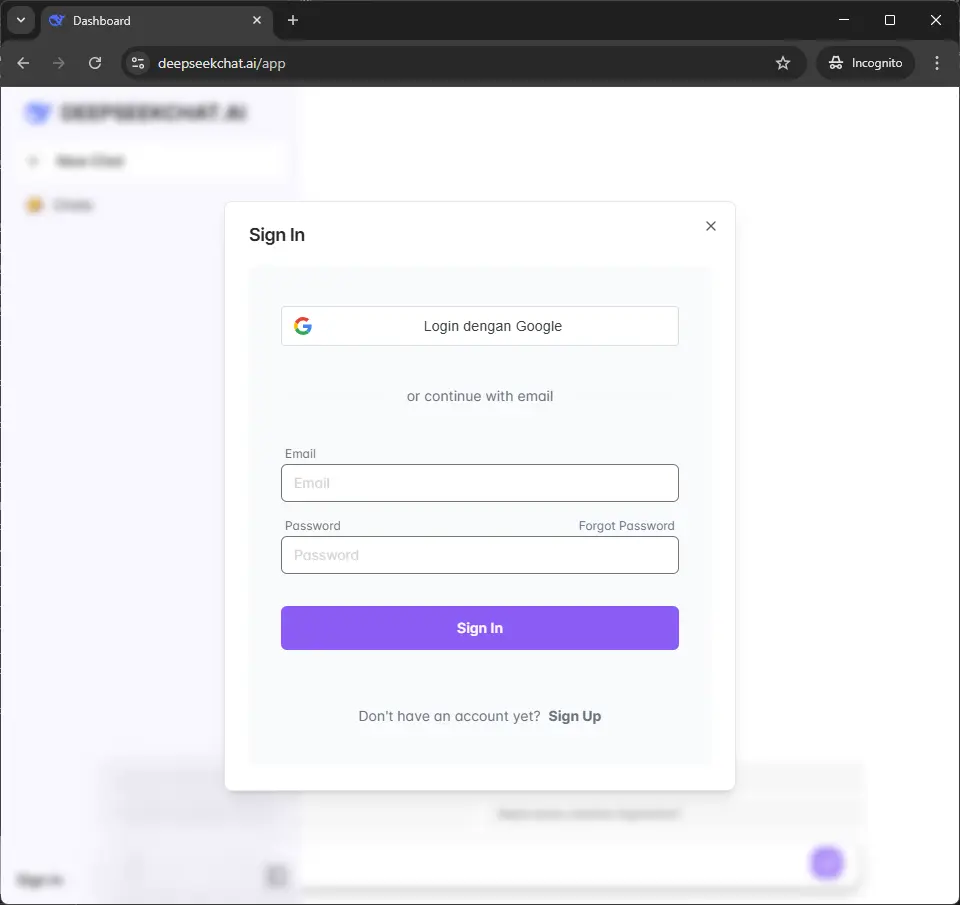
We're very interested in inspecting where our credentials being transmitted to using the Sign in with Google feature. Sadly, I can no longer replicate it at the moment, but someone else could. As expected, the request will be sent to an external service which may be controlled by the scammers.
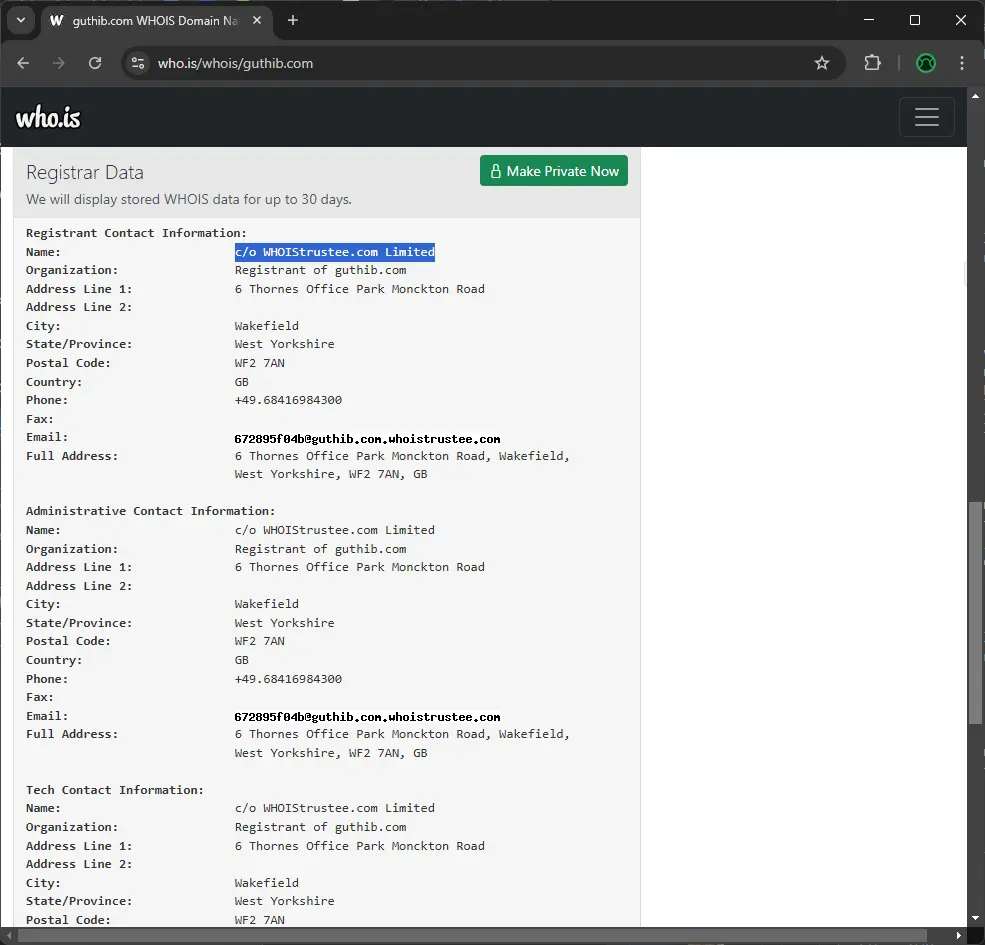
For companies, this kind of action can mean loss of traffic and credibility, which inevitably leads to loss of revenue. It’s a good idea to register common misspellings on your business domain, as some big companies like Facebook have done. There is an interesting case where someone reserved the misspelled domain name guthib[.]com for GitHub.
It turns out the good culprit is a company called WhoisTrustee.com which provides services to protect the identity of domain name registrants.
Interesting, isn't it?
Please, put a comma
If in the previous case it wasn't known how big exactly the losses were, in this type of case the report is already widely known on the internet.
Before we jump into the case, let's have a look at the following chat on a Reddit subforum.
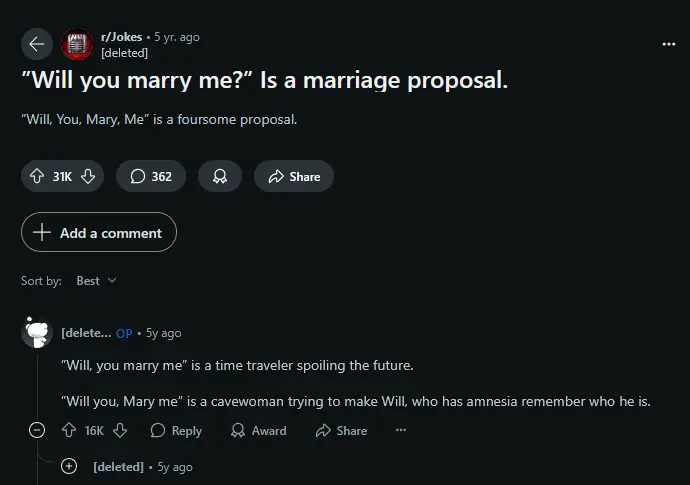
Ha-ha! So be sure that you care more about commas. Okay, time to get serious.
BBC had reported several cases on this topic. Let's read the following law:
"... the canning, processing, preserving, freezing, drying, marketing, storing, packing for shipment [there's no comma here] or distribution of: 1) agricultural produce; 2) meat and fish products; and 3) perishable foods ..."
The law stipulates that overtime pay does not apply to workers involved in such actions. Since a comma was missing there, it cost $5 million to a dairy company in Portland, Maine, USA, due to years of unpaid overtime claims.
There are some more cases in the BBC report, but the pattern is no different.
A couple of similar cases reported by Typing.com. Where a missing hyphen in NASA code lead to $80 million loses in 1962. Another time, Taylor & Son Ltd. was mistakenly entered into a database as Taylor & Sons. The extra "s" cost the 124-year-old engineering firm $14 million.
In 2012, one of Boeing's patents was revoked for a misplaced comma. The patent was about a method for handling aircraft communications. This is not only a patent loss, but also a loss of business due to the inability to stop their competitors from practicing the publicly invention.
Seems ... no doubt
I know it's my fault for not writing this article sooner. So, once again, I missed the opportunity to take screenshots of the evidence myself.
Anyway, this type is not much different from the former. This involves the impersonation of Visual Studio Code extensions. However, this case has actually been known for a long time in other marketplace such as PyPI for Python.
Discovered by Aqua Nautilus researchers, a popular extension called Prettier had been challenged by a fake one. Look at how similar these two things are:
https://marketplace.visualstudio.com/items?itemName=esbenp.prettier-vscode
https://marketplace.visualstudio.com/items?itemName=espenp.pretier-vscode
Let's clear it up:
esbenp.prettier-vscode // legitimate espenp.pretier-vscode // fake
It's only one letter off from the publisher's name and the extension identifier. That's rather difficult to tell the two apart, don't you agree?
In summary, we cannot underestimate any mistake, no matter how small, no matter how silly. But the most important thing is to never trust anyone who suggests executing rm -rf /, never, ever.